How a CDN Protects Your Website From DDoS Attacks

This blog explains how CDNs defend against DDoS attacks, the mechanics behind their protection strategies, and why they’re essential for modern web security.
Distributed Denial of Service (DDoS) attacks are one of the most common and damaging threats websites face today. They overwhelm your servers with traffic, disrupt availability, and can take down even well-architected applications if left unmitigated. And the threat is only getting worse.
What makes them especially dangerous is how cheaply and quickly they can be launched, targeting businesses of all sizes with minimal effort from attackers. Traditional web servers often lack the scalability and response mechanisms needed to fend off such attacks. That’s where Content Delivery Networks (CDNs) step in.
CDNs aren’t just built for performance, they’re also designed for resilience. In this blog, we’ll break down how a CDN protects your website from DDoS attacks, the tactics it uses, and why integrating one is critical for safeguarding your user experience.
What Are DDoS Attacks?
A Distributed Denial of Service (DDoS) attack aims to make a website, application, or service unavailable by flooding it with massive amounts of traffic from multiple sources. Unlike a simple DoS attack from a single origin, DDoS attacks leverage botnets (networks of compromised systems), to launch coordinated traffic spikes that overwhelm server resources, bandwidth, or application logic.
There are several types of DDoS attacks, including:
- Volumetric attacks: Saturate the network’s bandwidth with UDP floods or DNS amplification.
- Protocol attacks: Exploit weaknesses in network protocols (like SYN floods) to exhaust server resources.
- Application-layer attacks: Target specific parts of a web app (like HTTP requests) that are resource-intensive to process.
The consequences go beyond downtime. DDoS attacks can lead to lost revenue, damaged reputation, and even vulnerabilities being exposed during the chaos.
For a deeper dive into how DDoS attacks work, and the risks they pose, read our full guide: What Is a DDoS Attack?
What Is a CDN and How Does It Work?
A Content Delivery Network (CDN) is a distributed network of edge servers placed across multiple geographic locations. Its primary role is to cache static content closer to users, speeding up load times, reducing latency, and balancing traffic loads efficiently. When a user requests content, the CDN routes the request to the nearest server instead of the origin, improving performance and reliability.

While performance is the most visible benefit, CDNs also play a critical security role. Their ability to absorb and distribute large volumes of traffic makes them ideal for mitigating threats like DDoS attacks, which often rely on overwhelming a single point in the network.
Want to learn more about CDN internals and architecture? Read our full guide: How a CDN Works
How a CDN Helps Mitigate DDoS Attacks?
Here’s how CDNs strengthen your security posture:
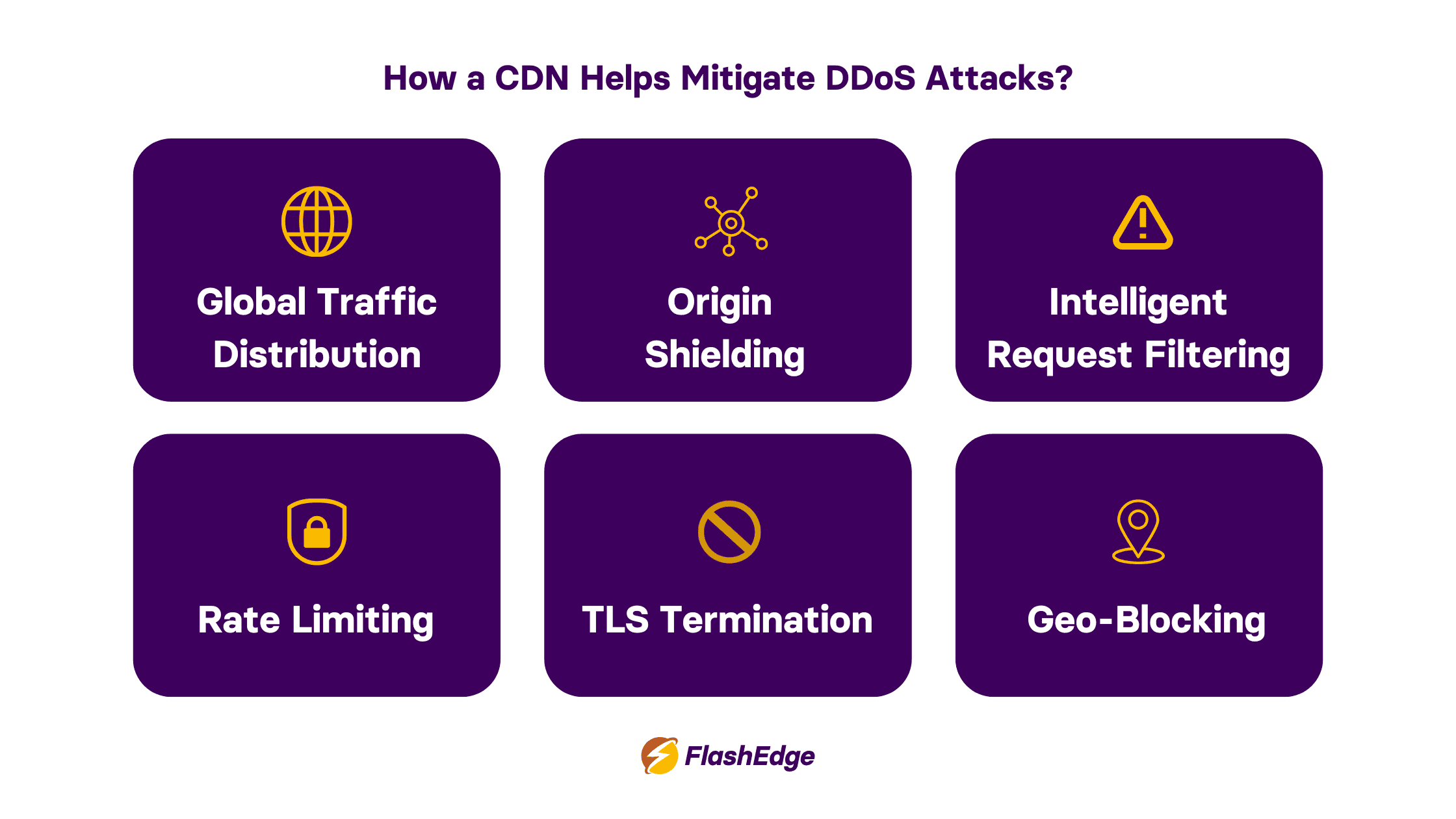
1. Global Traffic Distribution
CDNs operate through globally distributed Points of Presence (PoPs). During a DDoS attack, instead of all malicious traffic hitting your origin server directly, the traffic is dispersed across a wide network. This distributes the load and prevents any single point from becoming overwhelmed. The scale of a CDN makes it incredibly difficult for attackers to saturate your infrastructure.
2. Origin Shielding
The CDN acts as a buffer between your origin server and the outside world. By serving cached content at the edge, it minimizes direct exposure of your core infrastructure. Even during an attack, your backend resources are protected from excess traffic, keeping them stable and responsive.
3. Intelligent Request Filtering
CDNs leverage WAFs (Web Application Firewalls) and IP reputation databases to block known malicious actors. Advanced CDNs use machine learning and behavior-based rules to distinguish legitimate users from bots or attackers, filtering harmful requests at the edge before they cause harm.
4. Rate Limiting and Challenge-Response Mechanisms
CDNs can apply rate-limiting policies that control how frequently users (or bots) can make requests to your site. For unusually high volumes, the CDN can trigger challenge-response mechanisms like CAPTCHA or JavaScript challenges, which deter automated attacks without affecting real users.
5. TLS Termination and Protocol Hardening
By terminating TLS/SSL at the edge, CDNs absorb the computational load of encrypted traffic, which is often exploited in HTTPS-based DDoS attacks. They also enforce secure protocols, reducing the attack surface related to older, vulnerable versions of HTTP or TLS.
6. Geo-Blocking and Custom Rules
Many CDNs allow you to geographically block traffic from suspicious regions or apply custom firewall rules based on traffic source, header anomalies, or request patterns. This tailored approach helps isolate threats before they escalate.
7. Faster Incident Response
Because CDNs centralize and standardize traffic management, incident response is faster. Whether it’s applying new rules, blocking IPs, or analyzing attack patterns, the CDN’s dashboard and controls give your team agility and visibility.
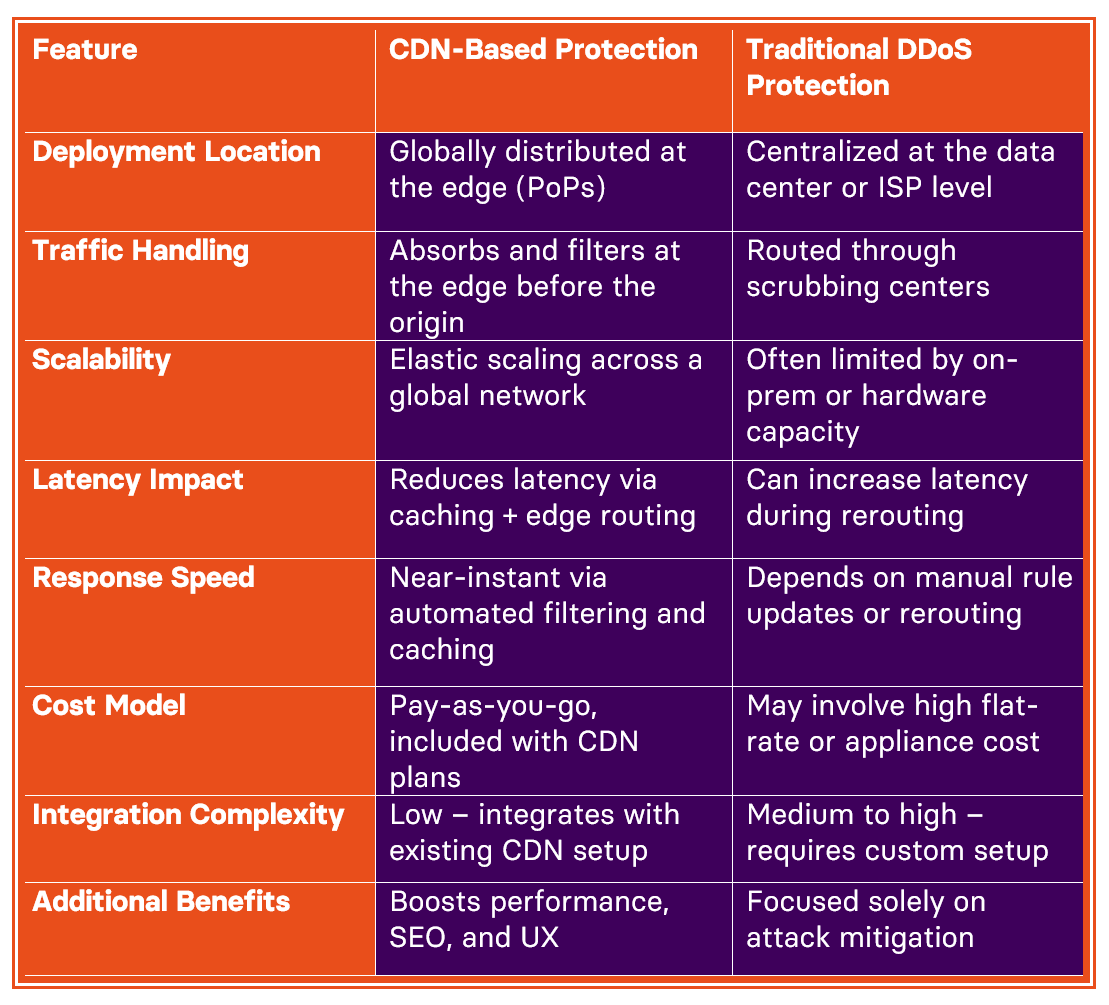
CDN vs Traditional DDoS Protection
Leverage a CDN With Built-In DDoS Protection
FlashEdge CDN offers built-in DDoS protection to analyze traffic in real time, blocking malicious activity while allowing legitimate requests to pass through. It elevates this protection with an enterprise-grade network optimized for robust security and performance. With over 700 Points of Presence (PoPs) worldwide, FlashEdge absorbs high volumes of traffic, neutralizing potential threats before they reach your servers.
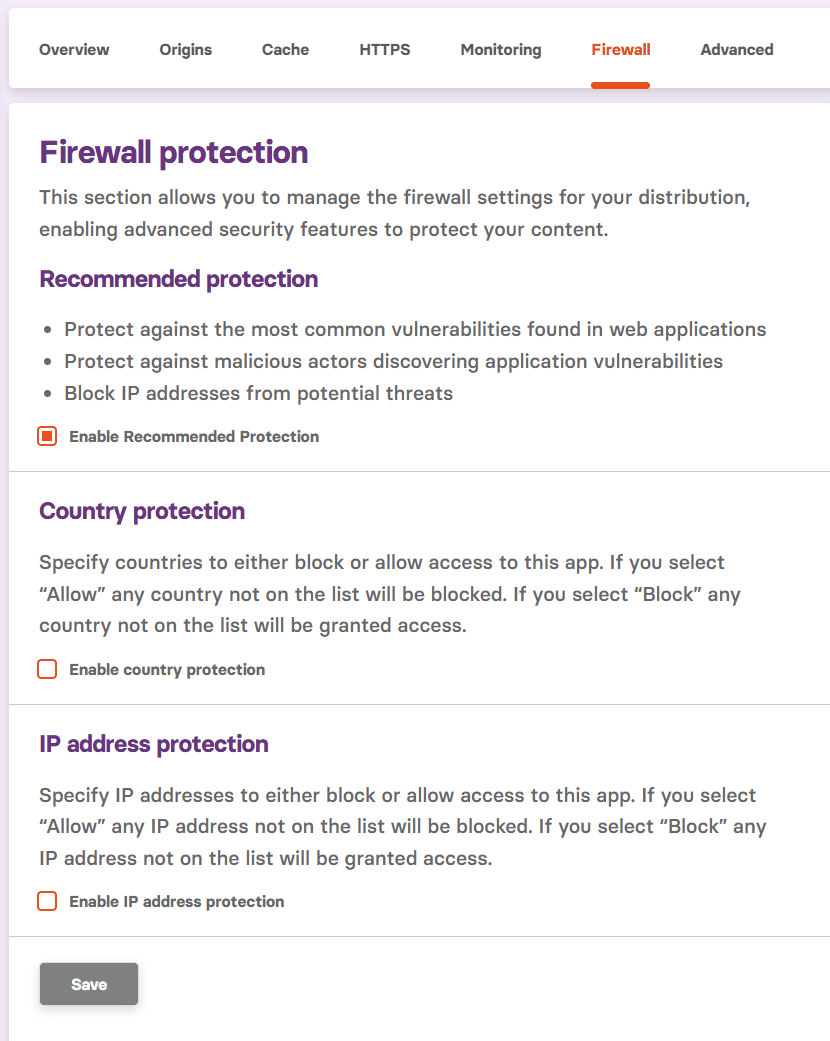
Additionally, FlashEdge now provides protection on the 7th application layer through a simple implementation in the FlashEdge Console. The FlashEdge WAF (Web Application Firewall) is built into the FlashEdge CDN and helps protect your content and applications against common web threats, including Layer 7 (application layer) attacks from known IP addresses, unwanted IP access, and traffic from undesired countries.
This feature is available under the Firewall tab for each distribution separately within the FlashEdge CDN console. You will find deeper information in our documentation.
Beyond security, FlashEdge offers a robust set of features like advanced caching, reduced latency, and cost-efficient, pay-as-you-go pricing.
Start your free trial today and experience unparalleled DDoS protection and performance with FlashEdge CDN.
FAQs
1. What is CDN DDoS protection?
CDN DDoS protection refers to the ability of a Content Delivery Network to absorb, filter, and block malicious traffic at the edge, before it reaches your origin server. This helps maintain site availability during an attack.
2. How does a CDN mitigate DDoS attacks?
A CDN mitigates DDoS attacks by distributing traffic across its global PoPs, filtering abnormal spikes, blocking known attack patterns, and caching content to reduce origin load. This minimizes the risk of server overload. It can also include specific functionality such as challenging suspicious traffic with CAPTCHA or blocking requests based on the reputation of the IP address.
3. Does a CDN stop all types of DDoS attacks?
While CDNs are highly effective against volumetric and protocol-based attacks, they may not stop sophisticated application-layer attacks without additional security measures like WAFs or behavior-based detection systems.
4. Is CDN protection enough on its own?
For most sites, a CDN offers strong baseline protection. However, for high-risk or regulated environments, combining CDN defense with dedicated security best practices, DDoS mitigation tools and web application firewalls is recommended.
Ready to start your journey to low latency and reliable content delivery?
If you’re looking for an affordable CDN service that is also powerful, simple and globally distributed, you are at the right place. Accelerate and secure your content delivery with FlashEdge.
Get a Free Trial